What is ‘Shadow IT’?
Shadow IT refers to the various web tools informally in use within most organisations. These tools are often chosen without reference to IT or to management in general.
They are often used for all the very best reasons. Your colleagues have work to do, and these tools help them, so they get used. You might know about some because there is a subscription charge, but others might be free.
These tools can be anything from simply keeping lists of tasks to do, sharing information or managing workflows, providing newsletter lists, or recruiting staff. Its endless.
There’s all sorts of web pages out there that your people will be finding useful and will be using.

The question is, do you know what is being used on your behalf?
Even more importantly, do you know who’s got access to them? As your staff come and go, do you know to change passwords or reset user accounts to make sure that no one who has left you (maybe even gone to a competitor) is still able to access your confidential data?
Shadow IT is one of the largest threats to data privacy in organisations today. It’s not necessarily because these sites are going to be hacked, although it’s always possible, but it’s because if you don’t know the tools are in use, then there is no way that you can manage them!
The first step to maintaining this data is to identify them, and that’s why you need new tools that are cloud focused.
If you’re still using the same old security tools that you used prior to the cloud, then you are simply not keeping up and we need to talk!
Here’s a story about what happens if you don’t have this under control: Why you need to know all the cloud services that your organisation uses – IT Solutions and Managed Services (kinetics.co.nz)
Shadow IT is part of our 10-point cyber-security check list
While there is no single layer of technology that can guarantee you will be safe from hackers, you can reduce your risk by adding layers of protection. How many of our 10-point check list are in place for you?
Real world Cyber-Security stories from the battlefront.
Every day we’re seeing more and more hacking attempts against clients. Cyber security attacks are getting more frequent, more threatening, and much more sophisticated. But for all that, and for all the associated risks, we’re astounded by the number of organisations...
Have you heard about “typosquatting”?
"Typosquatting" is the name given to criminals pretending to be someone they aren't - taking a domain name that uses a clever combination of legitimate-looking original sender email addresses, with spoofed display sender addresses that contain the target usernames and...
Preparing for a sudden Covid19 Delta Lockdown in New Zealand
Every week that we don't go into lockdown seems like a blessing. It can only be a matter of time before NZ is thrown back to a tight, restrictive lockdown. If, as we read yesterday, every Covid case coming in through the New Zealand border right now is infected with...
Cyber-war Seminar
Stories from the Cyber-war The simple reality is that cyber-crime is now a mega-business. The cost and effort to combat it grows all the time. "Is it worth it?" Good question. Every organisation needs to choose a level of security and resulting cost, effort and...
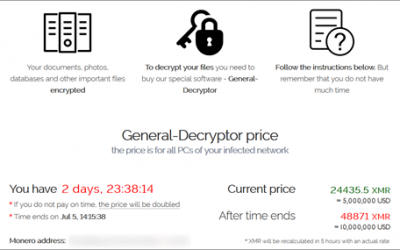
What you need to know about the massive global ransomware cyber-attack over the weekend
The Risk Is Real. Over the weekend, thousands of businesses were caught up in a global cyber-attack that is being blamed on a Russian hacker group called Revil. It is disappointing when geo-politics impacts everyday business, and the reports talk about President Biden...
(yet) another reason Why paying ransomware demands hurts. (The FBI agrees)
We don't negotiate with terrorists Recently, we asked the question if organisations should pay ransomware demands. There is a balance between desperation and the uneasy knowledge that you might be funding further criminal attacks on the community. We’ve just read a...
Pretending to be you or your colleagues
Just because it seems safe, doesn't mean it is. On some emails, you might see a warning that marks them as being ‘external’. This gets added as the email comes into your organisation. The idea is a simple one – if you see an email marked as external, then you will be...
Avoiding ad trackers when you browse the ‘net
Your own personalised stalker It always seemed slightly creepy that your computer shows advertising that is strangely accurately targeted at things you might have been interested in. On the surface, that seems quite useful. If you have to tolerate ads on your...
Phishing emails are getting smarter every day
In the old days (ie last year!!), a dodgy email had a whiff to it – there was something that triggered your subconscious. That’s because some phishing emails were really badly written with terrible English. But others just had a sniff about them- something that made...
A cyber-criminal only needs to get lucky once. You have to stay ahead of them all day, every day
"A cybercriminal only has to be lucky once, while a defender has to be lucky every minute of every day.” - Combating Ransomware - A Comprehensive Framework for Action: Key Recommendations from the Ransomware Task Force. The message we hear from governance boards over...