This sounds like a nightmare that could never happen.
US soldiers have been putting sensitive information online in non-secure third party websites. It defies belief, yet we’re reading that it happened. The story popped up on ‘Gizmodo’ .
It is alleged that US Soldiers were saving sensitive information on a couple of common flashcard sites, presumably of things they were trying to memorise and learn. It seems these are common learning tools used in universities to help students memorise facts. That works well so long as the facts aren’t top secret! Even worse, their settings were on ‘public’ not ‘private’!

It is a classic warning about the risk of people, however well intentioned, saving critical data online in places the organisation is unaware of, and can’t control. That’s why our KARE FOUNDATION proactive cyber-security plan helps identify use of these sites in your organisation.
For more detail : Why you need to know all the cloud services that your organisation uses – part 2 – (US DoD Nuclear Secrets!) – IT Solutions and Managed Services (kinetics.co.nz)
Shadow IT is part of our 10-point cyber-security check list
While there is no single layer of technology that can guarantee you will be safe from hackers, you can reduce your risk by adding layers of protection. How many of our 10-point check list are in place for you?
Breaking news: New protections added to Kinetics KARE Foundation
We have big news for Kinetics customers on our “KARE Foundation” cyber plan. We've added new Browser Cyber-Protection We’ve found an amazing new security tool called ‘Conceal' that provides even more added protection. Cyber-security is all about layers and this one...
Penetration Testing
Penetration testing is important for businesses because it helps them identify and fix security vulnerabilities before they can be exploited by attackers. It can be a significant job as it needs a team of security professionals to simulate a real-world cyberattack....
What would you do?
Imagine – you are busily going about your day when suddenly your meeting is interrupted. “No one can access their files!!!” or “We just accidently paid $50,000 to a fraudulent account and we can’t get it reversed!!!” or something similar. What would you do? Where...
Security Updates
We need to make some security changes. These are in accordance with the continued work by Microsoft to protect 365 users. This will keep your configuration current with their latest advisories but may have some (limited) impact on your IT experience. It is all about...
Layered Security Works
There is no silver bullet in cyber-security. Best practice requires layers of protection. One of those layers is ‘geo-blocking’, which means you can only log in from specified countries and overcomes many of the African and Eastern European hacker fraternities....
Look out for LinkedIn Smart Links
This is a great example of needing new tools that didn't used to exist, to keep cyber-safe, even if they add cost to our cyber-protection. Hijacking your trust in LinkedIn Cybersecurity firm Cofense have detected phishing campaigns that used LinkedIn links called...
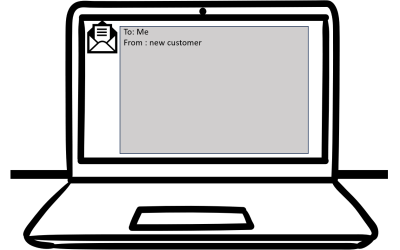
Would your cyber-security have saved you from this hack attempt?
This is a real and very clever 'spear-phishing' attempt that one of our legal clients in Auckland received today.Would you have opened it? Would your IT have protected you?To: Me From : new customer Hello, My Husband and I are looking to buy a property (First-time...
Is it really you?
News that an elderly woman was tricked out of $100,000 over Facebook won't be a surprise to regular readers. She was fooled into thinking she was talking to a friend, and then sending money to access some make-believe Covid fund. AI makes it easy to speak in...
Ransomware claims increase 27%
The Coalition Insurance "2023 Cyber Claims Report: Mid-year Update" highlights the changing nature of the cyber threat landscape that businesses are currently facing, with a record surge in claims severity compared to the previous year. This is US data but it tends...
Webinar Replay : Learn How to Protect Yourself from the Darkweb Now
What does it mean If your personal details are leaked on the darkweb? Learn how you can manage your risks.The darkweb is a network of websites and servers that are not indexed by traditional search engines and require special software to access. It's a place where...