The world is changing.
Your company’s cyber security is increasingly under threat and the costs of mitigation are often unwelcome. The first question organisations need to ask is whether they are exposed, and to what level.
All the available data from sources like Cert-NZ and media reports indicate a growing trend and increased sophistication. Ransom threats now focus on breaching privacy rather than simply disrupting your operations.
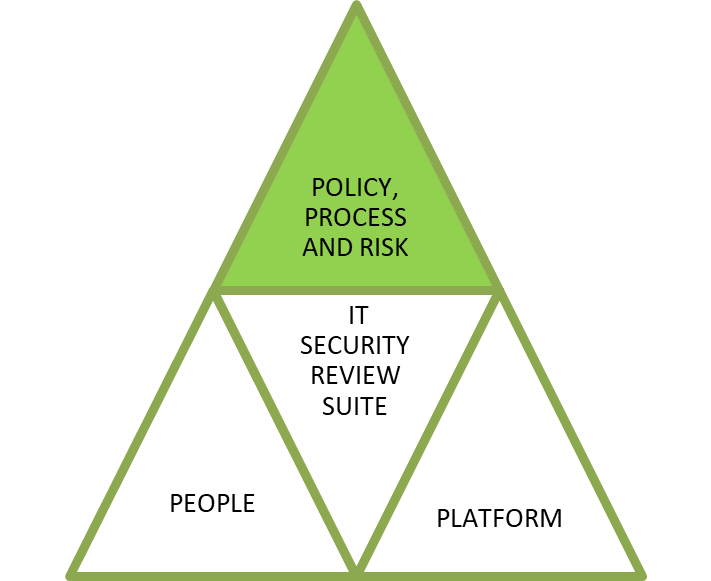
Kinetics recommends starting with an understanding of the nature of the risk exposure, and identifying how much value you assign to each risk and to then respond accordingly. Not everyone’s needs, or risk profile, are the same, and not all data has the same importance.
Start with an IT security review that considers your policy, process and business risk. Identify what security measures are important and how they apply to you.
wE recommend a Kinetics “IT Posture Security Review” to provide this reference point.
Next up is to look at your people – often you biggest risk. Often busy people are the most vulnerable simply because they are operating at speed, or because people are too trusting. Every day it seems the NZ Herald or Stuff websites have stories about people who have been scammed.
Do your people understand the steps necessary to protect themselves, and your organisation? How aware are they of the kinds of scams that they will be vulnerable to?
A Kinetics “People Review”typically evaluates awareness of phishing risk, dark web identity leakage, and an assessment of your ‘active directory’ identity database.
The outcomes may well be increased awareness programmes, scheduled testing and regular audits of your access controls. Simple practices such as ensuring your people have their system access limited to just what they need for their work also limits the exposure they might yield to a cyber-criminal. Another quick win is auditing the user account to ensure that only current staff and contractors have access to your data on all your most important platforms.
Finally, a technical assessment of your platform will help test how well your protections match the requirements you have already identified in the earlier reports.
Specifically, this review should look at the IT assets that you maintain directly, from the end-points that are used to access your systems to the physical and virtual servers that you maintain. It needs to include network and device scans for the presence of common vulnerabilities and benchmarking against industry standards
A Kinetics technical audit considers a number of elements, from the maintenance of assets and the existence internal and external vulnerabilities to the status of your current passwords and MFA security on your 365 presence.
Together,these three steps ensure that you have a full understanding of their cyber-security aspirations and most appropriate actions to meet these.
While there is always cyber-security risk and no one can absolutely promise to keep you safe from cyber criminals, there are things we can do to minimise the risk, some that relatively easy and quick and others that are more involved. We need to ensure you have appropriate protection to meet your needs as understood today, including any requirement from your cyber-insurance.
